
Importance
Currently, the increasing use of digital technology to support service provision, corporate management, and airport operations has made information technology (IT) security, system reliability, and privacy protection critically important. Any incident involving data breaches, system outages, or cyberattacks could cause significant harm to stakeholders and lead to a loss of trust in AOT. Moreover, such incidents may also constitute violations of human rights, specifically the right to privacy.
Policy
AOT has established the following policies to ensure robust information and communication technology (ICT) and cyber security all of which covers entire AOT operation and suppliers:
- AOT ICT Security Policy
- AOT Cyber Security Policy
- AOT Personal Data Protection Policy
- AOT Data Privacy Policy
These policies align with relevant legal and regulatory requirements. AOT ensures these policies are communicated to all employees and external parties working with AOT to raise awareness and emphasize the importance of maintaining IT security and protecting personal data. In addition, AOT regularly conducts risk assessments and security testing of its systems. The company is also certified under ISO/IEC 27001:2013, the international standard for information security management systems.
AOT ICT Security Policy
AOT’s ICT Security Policy emphasizes ensuring the confidentiality, integrity, and availability of its ICT systems. The policy covers access to information systems, networks, operating systems, applications, and data. It mandates regular risk assessments and audits, monitoring and responding to information security threats, along with the development of contingency plans to maintain business continuity and uninterrupted access to information.
All AOT employees and external parties working with AOT are required to acknowledge and comply with this policy to uphold the organization’s ICT security standards.
AOT Cyber Security Policy
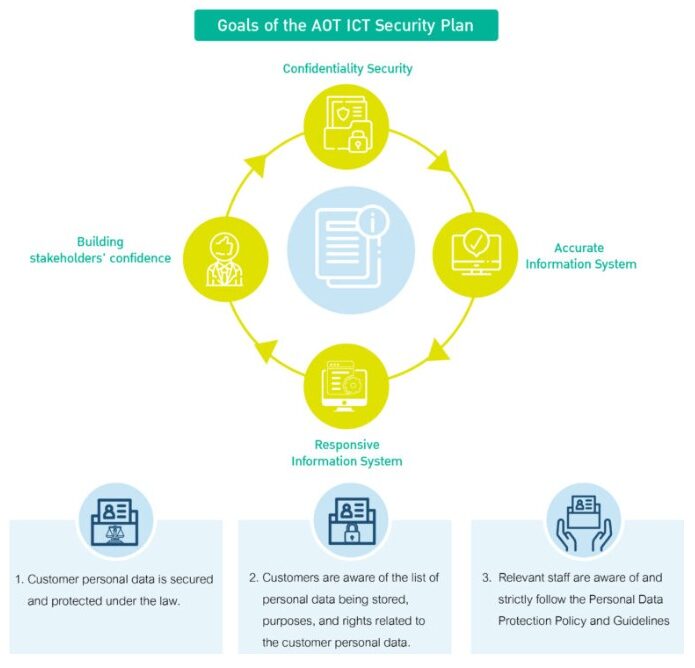
In 2021, AOT established its Cyber Security Policy to ensure robust cyber resilience in preventing, responding to, and mitigating risks from cyber threats—whether domestic or international—that could impact AOT’s operations or services. These threats may pose risks not only to AOT but also to national security and economic stability.
The policy aligns with the guidelines and national cybersecurity strategy set forth by the National Cyber Security Committee, ensuring that AOT’s approach is consistent with the broader framework for maintaining cyber safety across critical infrastructure sectors.
AOT Personal Data Protection Policy
AOT has established its Personal Data Protection Policy to ensure the security and confidentiality of personal data related to electronic transactions. This policy covers the personal data of AOT employees, external personnel working with AOT, and service users for the entire operations, which also include suppliers. It is reviewed regularly, at least once a year or as necessary. The President of AOT or a designated senior executive is responsible for issuing the policy, supporting operational practices, overseeing implementation, monitoring compliance, and providing guidance. Any violation or breach of this policy is considered a disciplinary offense under AOT’s internal regulations (Disciplinary Actions in Case of Breach). The Personal Data Protection Policy is also embedded in the company’s risk compliance.
The AOT Personal Data Protection Policy aligns with the Royal Decree on Criteria and Procedures for Electronic Transactions of Government Agencies B.E. 2549 (2006), the Electronic Transactions Commission’s Notification on Policy and Guidelines for Personal Data Protection of Government Agencies B.E. 2553 (2010), the OECD Guidelines on the Protection of Privacy and Transborder Flows of Personal Data, and internationally recognized practices for data privacy.
AOT informs users of its mobile applications about data privacy through official Terms of Use and Privacy Policies, as well as its publicly available Cookies Policy on AOT’s official website.
Management Approach
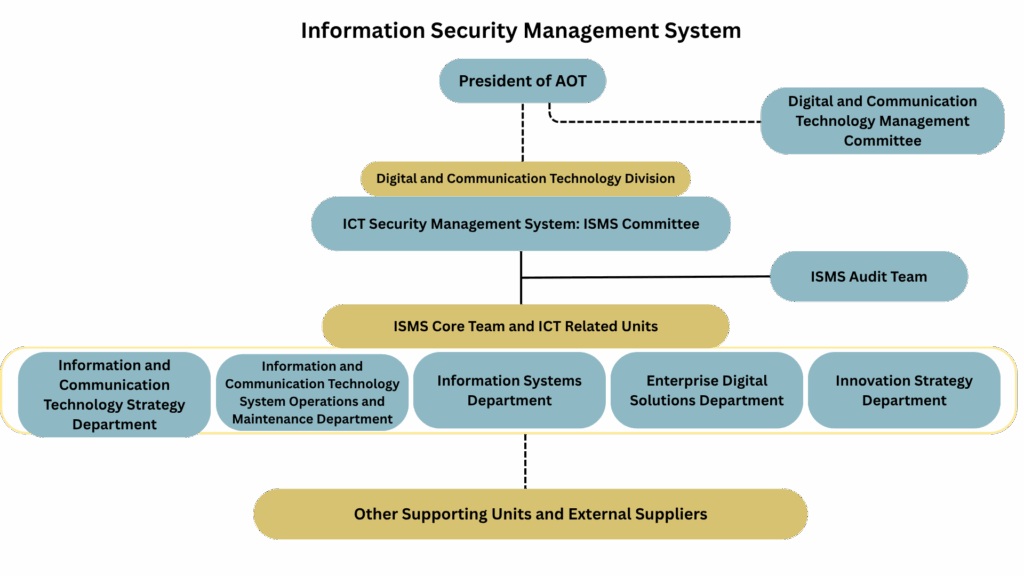
Information Security and Data Privacy Governance Structure
- The organizational structure for information security and data privacy at AOT is divided into three levels, as a designated person or department responsible for information security and privacy issues
- Board Level
- Executive Level
- Operational Level.
It comprises the following bodies:
- AOT Digital Technology and Communication Management Committee
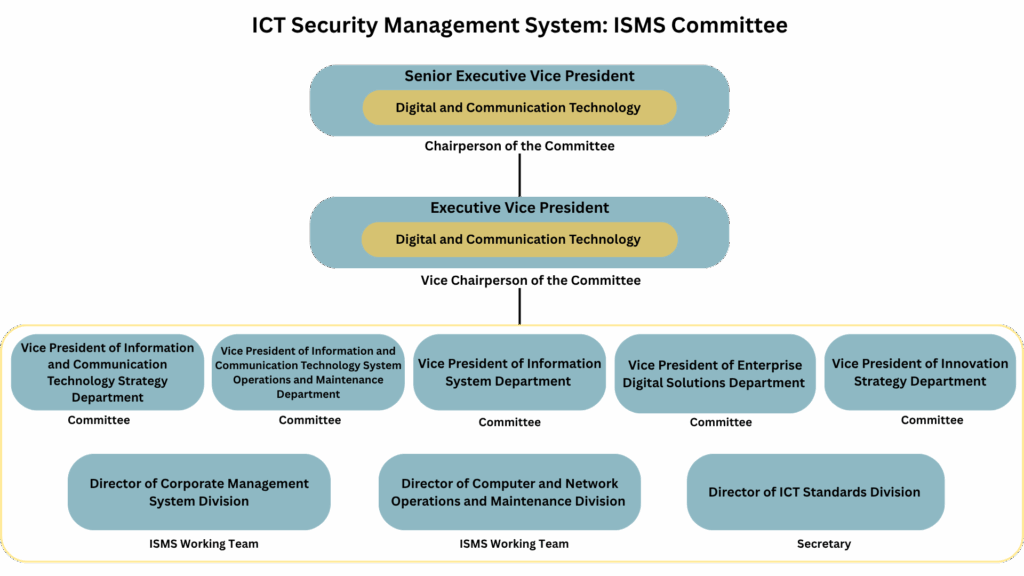
- AOT Information Security Management System (ISMS) Committee
- AOT ISMS Team
- AOT ISMS Audit Team
- Working Group Supporting the Duties of the Data Protection Officer (DPO)
- Information and Communication Technology (ICT) Division
Board Level
| Personnel/Units Involved in Information Security and Privacy | Roles and Responsibilities |
|---|---|
Board of Directors: Associate Professor THIRA JEARSIRIPONGKUL Independent Director/ Audit Committee Member Chairperson of the Data Security and Privacy Committee Also serves as a member of the AOT Digital Technology and Communication Executive Committee Relevant Work Experience in IT: - Chairperson of the AOT Digital Technology and Communication Executive Committee Term of service: 3 April 2024 – 26 February 2025 IT-Related Education and Training: - Digital Transformation for CEO #3 (DTC#3), organized by Krungthep Turakij, Thansettakij, and MFEC Public Company Limited - IT Governance and Cyber Resilience Program (ITG), Class 12/2019 Board Skills Matrix: Science and Technology/Telecommunications and Information Technology/Innovation  Independent Director Chairperson of the Data Security and Privacy Committee Relevant Work Experience in IT: - Chairperson of the AOT Digital Technology and Communication Executive Committee Term of service: 26 February 2025 - Present - Consultant in Technology and Innovation to the Minister of Digital Economy and Society (Mr. Prasert Jantararuangtong) Board Skills Matrix: Science and Technology/Telecommunications and Information Technology/Innovation  Mr. Mr.KERATI KIJMANAWAT President Vice Chairperson of the Data Security and Privacy Committee Also serves as a member of the AOT Digital Technology and Communication Executive Committee Relevant Work Experience : Vice Chairperson of the AOT Digital Technology and Communication Executive Committee IT-Related Education and Training : - Training Course on Readiness for Compliance with the Personal Data Protection Act B.E. 2562 (PDPA) for AOT Executives, Fiscal Year 2022 |
|
Executive Management
| Personnel/Departments Involved in Information Security and Privacy | Roles and Responsibilities |
|---|---|
Executive Management: Mr.Kittipoj Venunantana Deputy President, Technology and Innovation Group (Chief Information Security Officer: CISO), serves as a member of the Information and Communication Technology Security Management System Committee (ISMS Committee) of AOT. |
|
Operational Level
| Personnel/Departments Involved in Information Security and Privacy | Roles and Responsibilities |
|---|---|
| Information and Communication Technology Security Management System Team |
|
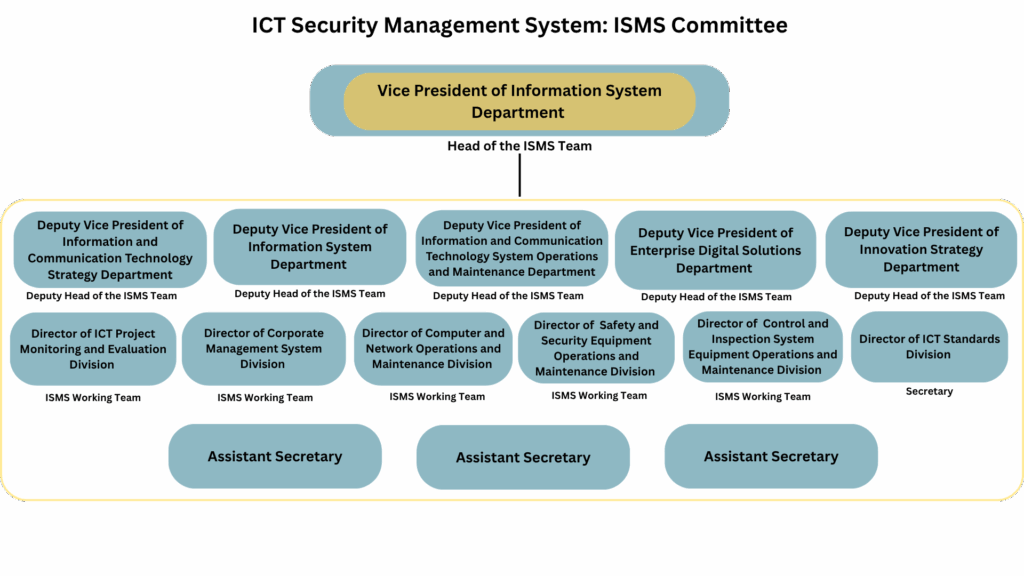
| Personnel/Departments Involved in Information Security and Privacy | Roles and Responsibilities |
|---|---|
| AOT Information and Communication Technology Security Management System (ISMS) Audit Team |
|
| Data Protection Officer Supporting Team: DPO Supporting Team |
|
Digital Technology and Communication Line
|
AOT has established Information and Communication Technology (ICT) security as one of the Key Performance Indicators (KPIs). Employees responsible for information security are required to complete organizational digital training courses—such as ISMS Awareness, Cyber Security, and PDPA—and their performance is evaluated on a scale of 1 to 5 (Level 1 = Needs Improvement; Level 5 = Excellent). This approach ensures alignment with the organization’s operational plans. |
AOT’s Information and Cybersecurity Guidelines
AOT has established comprehensive guidelines to ensure the security of information and information systems and control over escalation process for employees to report incidents, vulnerabilities or suspicious activities.. These guidelines outline operational procedures for key activities, including:
- Procedures for transporting backup media
- VPN access request process to connect to AOT’s internal network
- Maintenance procedures for computer center support systems
- Guidelines for cryptographic practices and key management
- Procedures for user access control to information systems
- Information classification and corresponding handling procedures
- AOT Cybersecurity Guidelines and Framework
- Incident Response Plan (IRP) for server-related disruptions
- Procedures for managing information security events and incidents
- Cybersecurity Incident Response Plan
- Rapid Cyber Threat Incident Reporting Procedure
- ICT Business Continuity Plan (ICT BCP), which outlines procedures for AOT employees in case of incidents that pose risks to cybersecurity or business operations
In addition, AOT’s approach to information and cybersecurity includes mechanisms for evaluating violations of security policies and procedures. These violations are assessed as part of overall employee performance to ensure accountability and continuous improvement in cybersecurity practices, as well as apply disciplinary actions in case of breach
Information and Privacy Security Audits
AOT conducts information and privacy security audits at least twice a year (semi-annually), covering the organization’s information technology systems and outlining response measures for emergency incidents. Employees follow the Incident Response Plan (IRP) and Information Security Event and Incident Management Procedures through the following steps:
- Internal Audits are conducted under the framework of the Information Security Management System (ISMS) Committee, ensuring compliance with internal policies and controls and privacy compliance.
- External Audits are performed by third-party entities, involving vulnerability assessments simulated cyberattacks (Simulated Hacker Attacks), and privacy compliance to evaluate system resilience. These audits assess the risk exposure and verify compliance with international standards including:
- ISO/IEC 27001:2013 – Information Security Management System
- ISO 22301:2019 – Business Continuity Management for Airport Services
The responsible units are required to report annual audit findings and recommendations to the relevant committees to ensure that audit results are acknowledged and acted upon in a timely manner.
Implementation
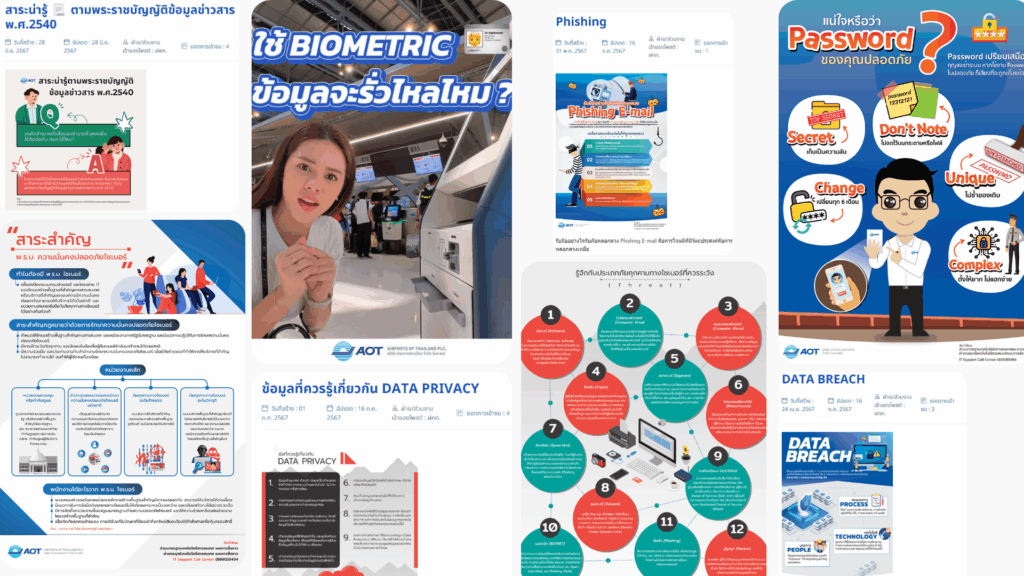
Awareness Media via AOT STAFF System
AOT has developed and disseminated information and privacy security awareness media through the AOT STAFF system to enhance employee awareness of information technology and privacy protection. The campaign includes various key topics, such as:
- 10 Things the Public Should Know About the PDPA
- Rights of Data Subjects Under the Personal Data Protection Act (PDPA)
- Who’s Who in the PDPA Framework
- Essential Information About Data Privacy
- Personal Data Processing in Employment Context
- AOT’s Complaint Channel for Personal Data Breach Incidents
- Is Your Biometric Data at Risk of Being Leaked?
- Key Points of the Cybersecurity Act
- AOT Data Management Guideline
- How Secure Is Your Password?
- Desk Organization and Screen Protection Tips
- 10 Best Practices for Protecting Your Information Assets
- Highlights of the Official Information Act B.E. 2540 (1997)
Information Technology and Privacy Training
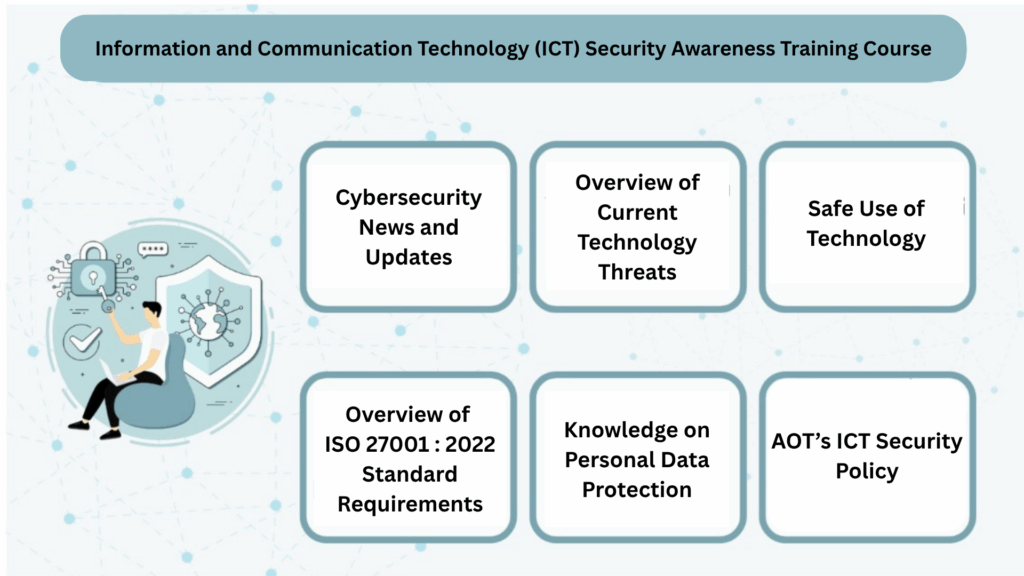
In the digital era, where information technology plays a pivotal role in driving organizational operations, enhancing knowledge and awareness in information and communication technology (ICT) security is essential. This ensures that personnel can work efficiently, safely, and in compliance with international standards. Additionally, training and preparedness in business continuity planning help mitigate and respond to technological threats that could impact AOT’s operations.
- AOT has implemented the Information and Communication Technology Security Awareness Training Program via an e-Learning system for AOT employees and staff. The training is conducted over a period of 1,230 days, aiming to equip personnel with essential knowledge aligned with ISO/IEC 27001 standards and to raise awareness of the importance of maintaining ICT security.
ICT Business Continuity Plan (ICT BCP) Drill
AOT conducts Business Continuity Plan (BCP) drills for Digital and Communication Technology Systems, covering six critical systems to ensure operational resilience and readiness in the event of disruptions. These key systems include:
- Log Data Retention System – in compliance with the Computer-Related Crime Act (No. 2), B.E. 2560 (2017)
- IT Infrastructure Consolidation System – covering both the main and backup data centers at AOT Headquarters and Suvarnabhumi Airport
- Electronic Document System (E-Document)
- Airport Safety Information System (e-Safety)
- AOT Application Programming Interface (AOT API)
- AOT Car Park Freezone System
Training on Personal Data Protection and Information Security Awareness
AOT has organized comprehensive training programs to enhance awareness and understanding of the Personal Data Protection Act B.E. 2562 (2019) among executives and employees across its six airports and headquarters. The training aims to provide legal knowledge, ensure compliance with the Act, and introduce necessary organizational measures, including general and information security-related controls to be implemented within AOT’s operations.
Additionally, AOT conducted training sessions to prepare personnel for the development of the Information Security Management System (ISMS) under the consultancy project for establishing ISMS in alignment with ISO/IEC 27001 standards. These training sessions covered seven core courses, designed to equip AOT staff with knowledge of best practices and compliance requirements in information security, relevant laws, regulations, and internal policies. The key topics include:
- Development of the Information Security Management System (ISMS) and ISO/IEC 27001 Requirements
- Roles and Responsibilities in Developing and Maintaining ISMS under ISO/IEC 27001
- Information Security Risk Management
- Information Security Lead Implementer Training under ISO/IEC 27001
- Information Security Management System (ISMS) Auditor/Lead Auditor Training
- Information Security Awareness for Executives and Employees at all seven AOT entities: Headquarters (HQ), Don Mueang International Airport (DMK), Chiang Mai International Airport (CNX), Phuket International Airport (HKT), Hat Yai International Airport (HDY), Mae Fah Luang – Chiang Rai International Airport (CEI), and Suvarnabhumi Airport (BKK)
- Personal Data Protection Awareness Training in compliance with the Personal Data Protection Act B.E. 2562 (2019)
Training Collaboration Project between AOT and the Cyber and Infrastructure Security Group (CISG)
- CISG delivered 10 laptops pre-installed with CARSA X-ray Tutor Software to AOT under the “Enhancing AOT Security Screener Capability” project. The purpose is to utilize the laptops for training new staff and conducting refresher courses, thereby enhancing the ability of screeners to detect prohibited items.The training also provides screeners with hands-on practice to improve their image analysis skills, covering both hold baggage screening and cabin baggage screening.
- The Operational Cyber Security in Aviation workshop aims to provide AOT personnel responsible for managing computer systems and information technology with in-depth knowledge and enhanced skills in assessing and mitigating risks, as well as preventing potential cyberattacks targeting systems, infrastructure, and information.
- The Aviation Cyber Security workshop is designed to raise awareness of security practices related to cyberattack prevention. It also aims to enhance knowledge of cyber threats (Cyber Attacks) and cybercrime, including various methods of cyberattacks and vulnerabilities that may expose an organization to such threats. The workshop emphasizes risk assessment in operations and identifies strategies to mitigate potential risks.
